Almost every time I’m working on network stuff in iOS or Android, I immediately open up Fiddler. I know that there’s also Charles Proxy for OS X which does just as well as Fiddler, but the majority of the time, my Windows VM is running anyway, so I just haven’t been able to justify the $50 for Charles Proxy when Fiddler is free.
When I’m working on networking stuff in iOS or Android, I don’t like treating networks as a black box. I do my web request and even if everything is giving me 200’s and looks like it’s working, it’s still a good idea to check the connection to be absolutely positive that you’re sending and receiving what you expect. If all goes well, you spend a few extra minutes looking at network transactions and pat yourself on the back for a job well done. But if things aren’t going perfectly, it makes things a whole lot easier to debug.
So here’s the steps I use to get things set up to be able to look at http/https traffic from my mobile devices. You can also easily extrapolate the steps to allow any device to go through your Fiddler install.
Install Fiddler
Even if you have Fiddler installed, you should still read this section because there’s more too it than you may expect.
Head over to Fiddler’s download page to get the latest version. Download the .Net 4 version. I have never had to download the .Net 2 version of Fiddler, and unless you are working in the stone age, you shouldn’t need it either. -Note: I’m sorry if I offended you if you are living in the stone age. But seriously, Windows XP is dead. What kind of person is trying to debug iOS/Android web traffic and is still running Windows XP?
Once you download and install Fiddler, there’s 1 more step. Fiddler’s default certificate maker doesn’t work out too well with iOS or Android devices. If you don’t care about decrypting https traffic, then there’s really no need to worry, but you might as well set things up completely to begin with. If you never have to decrypt https traffic then lucky you, but now days as a developer you’ll probably have to do it at least some time.
Fiddler has a wide array of Add-ons. Some of them are pretty nice, so I recommend taking a moment to glance at the page, but the only one that you need is CertMaker for iOS and Android. Here’s the direct download, but you should probably still head over to their site to make sure you get the latest version. Simply download it and run the executable to install the CertMaker.
Setup Fiddler
Now that we’ve got Fiddler and the CertMaker installed, we need to do a little bit of setup.
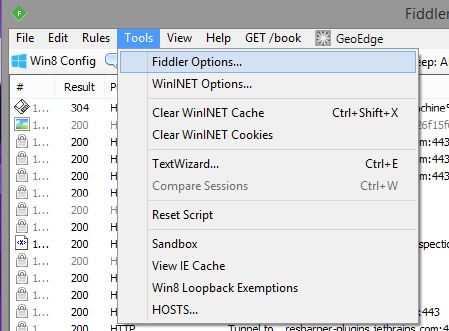
Open up Tools->Fiddler Options…
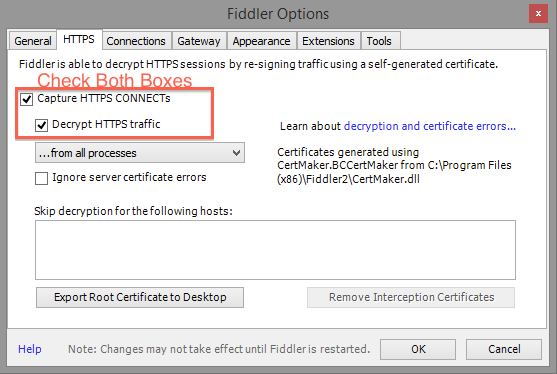
On the HTTPS tab, make sure the box for “Capture HTTPS CONNECTs” and “Decrypt HTTPS traffic” are both checked. The first time you do this, Fiddler will prompt you to make sure you want to trust the Fiddler Root certificate. Then Windows will prompt you, then Fiddler will prompt you again, then the certificate will finally be installed. You will need to say Yes on every one of those prompts. If you say No, then Fiddler won’t be able to decrypt your https traffic.
The reason for so many prompts is because allowing https traffic to be decrypted is a slight security hole. I’ve never had any issues with it in the years that I’ve been decrypting my own https traffic. If you are a particularly paranoid individual, you can uncheck “Decrypt HTTPS traffic” and then click the button labeled “Remove Interception Certificates” and that will remove the Fiddler Root certificate. Doing this, you could install the certificate only while you need it installed, and then remove it when you’re done decrypting your traffic. I don’t personally do this, but you are welcome to.
NOTE: on newer versions of Fiddler, there is an “Actions” button on the right side of this dialog, if you click on it has options to get Fiddler to install/uninstall the Fiddler root certificate. If you’re not interested in snooping your own traffic, you don’t really have to install the certificate, but its easier to just install it so you never have to go back and set it up later.
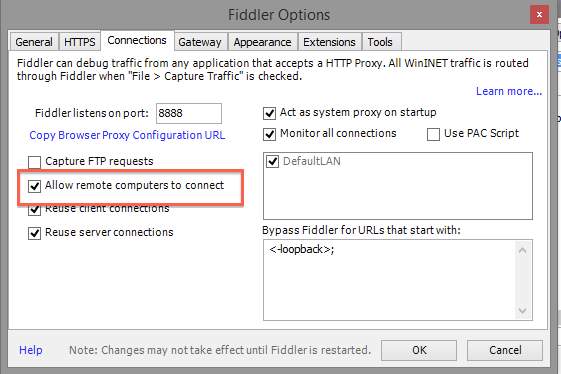
Next, go to the Connections tab. And check the box that says “Allow remote computers to connect”
Now you’ll need to restart Fiddler.
iOS Setup
On your iOS device, open up Safari (you must use Safari) and navigate to
|
1 |
http://<your computer>:8888/FiddlerRoot.cer |
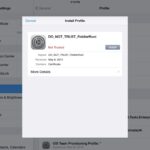
This will bump you into settings with a window to install the Fiddler certificate.
Ignore that the name of the certificate is “DO_NOT_TRUST_FiddlerRoot” you really can trust it. Press install, then install again, then type in your pin for your device.
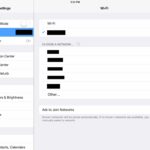
Now you need to go to your wifi settings and go to the properties for your network
And finally, set the proxy settings for the network
Now all of the https traffic on your iOS device will proxy though Fiddler.
Android Setup
Unfortunately for Android, the setup can vary from device to device. And on some devices, the OEM has made modifications to the OS to disallow user defined root certificates. The Sony Xperia is one we had particular trouble with at work. The basic steps (regardless of the platform) are:
- Install the Fiddler Root certificate onto your device to allow Fiddler to decrypt https traffic
- Set the proxy settings for your network
Some Android devices require you to jump through hoops to install the Fiddler Certificate, and all Android devices I’ve found require you to set a PIN or Pattern or what not in order to install the Fiddler Certificate.
Open up a browser, on Android it shouldn’t have to be a specific one, and navigate to:
|
1 |
http://<your computer>:8888/FiddlerRoot.cer |
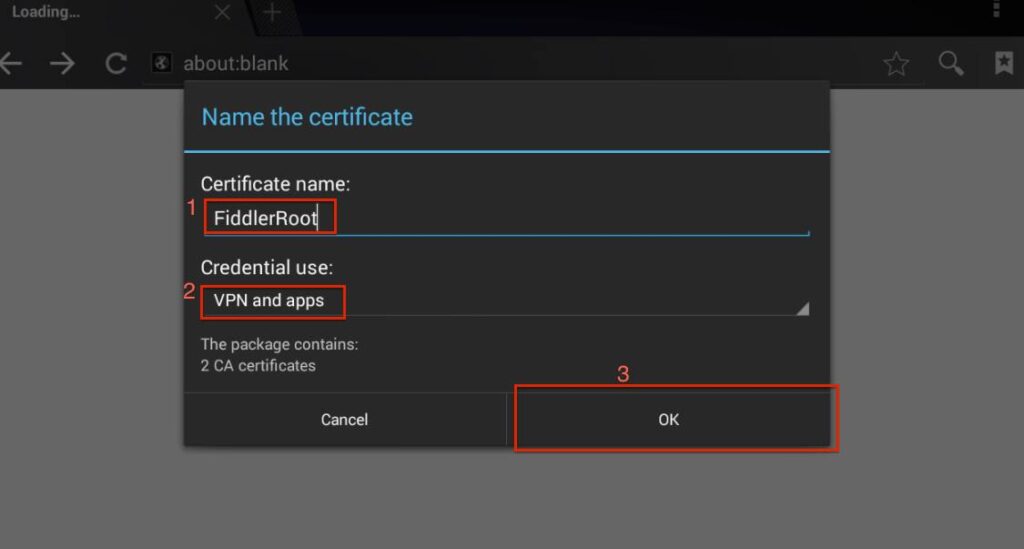
If you’re lucky, you won’t have to jump through any hoops to install the certificate. You’ll be presented with a prompt to name/install the certificate
Name the certificate something useful, make sure its set to VPN and apps for the credential usage and then tap OK. Once you tap OK, you may get some additional prompts from Android about a PIN or something, every Android device is different.
If visiting the URL to get the certificate downloads the certificate, but doesn’t start trying to install the certificate, don’t worry. It downloaded the certificate, it just didn’t try to install it.
- Open Settings
- Go to Security
- Scroll way down and tap on ‘Install from SD card’ or ‘Install from External Storage’ or whatever it says
This should open the same prompt as above. If it doesn’t you will need to consult with Google (good luck).
Once you’ve got the certificate installed
- Go to your wireless settings
- Long press on your network
- Select ‘Modify network’ from the modal dialog that opens
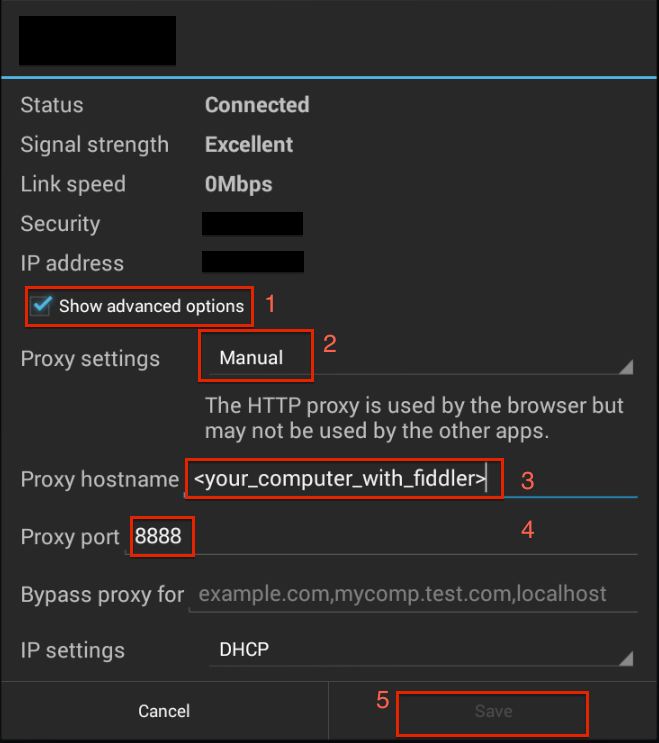
- Check ‘Show Advanced options’
- Fill out the proxy settings
In the image below, Save is disabled because I did not enter a proper hostname
Now all of the https traffic on your Android device will proxy though Fiddler.
Happy Debugging!

Hi, thanks for sharing. I am following the instruction above but when I tried to install the certificate on my iphone 5, “safari could not open the page because the server stopped responding”.
PS. I am on my company wifi, would that be an issue?
Any advice? Thanks
I’ve never had any issues doing this on company wifi. Our company even does ssl snooping of all traffic, which is pretty common in the enterprise world.
I would try hitting
http://localhost:8888/FiddlerRoot.ceron the machine that is running fiddler to make sure fiddler is working properly. If that doesn’t work, you might have fiddler set up to use a different port instead of 8888.Now that I think about it, it’s possible that your company wifi has a firewall that’s blocking all traffic on 8888. You could also try changing fiddler to use something like 8080 that’s normally used by tomcat. If it is a firewall problem, most firewalls allow 8080.
You could also check that you have “Allow remote computer to connect” turned on, and that you restarted Fiddler after you turned that on.
On your local computer (the one that generated the cert) go to http://:8888/FiddlerRoot.cer in a browser such as Chrome. This will download the FiddlerRoot.cer to your local computer. From there you can email yourself the FiddlerRoot.cer as an email attachment and open it from your iOS device and that will do the same thing. Click on the FiddlerRoot.cer attachment from the Mail app on your device and it will prompt you to install it.
After I do this and try to hit an SSL page on my iPad (I’ve imported the cert via Safari and verified iOS is hitting Fiddler), I get this message in the app:
The operation couldn’t be completed. (NSURLErrorDomain error -1012).
Fiddler only sees the SSL CONNECT to http://abc.somesite.com:443 and a connection closed response.
I believe iOS is not liking the certificate. This is Fiddler 4.4.9.9 running on Windows 8.1.
I’ve seen this happen when you don’t have the CertMaker add on installed in fiddler. Fiddler’s default method for creating certificates isn’t compatible with iOS, so you need to make sure you have the CertMaker installed so fiddler will make iOS compatible certificates. Add-ons and make sure you have the CertMaker for iOS and Android installed.
I’ve also run into issues with star certificates. When apps do SSL snooping, they decrypt the traffic and then they re-sign it with their own certificate. When re-signing, it creates a new certificate chain for the traffic. Sometimes there are issues with how star certificate traffic gets resigned and it causes a bad chain.
SSL pinning can also be a problem. With SSL pinning, an app will have the ‘proper’ certificate bundled with the app. When the app makes the SSL CONNECT, it compares the cert that it gets to the ‘proper’ cert, and since fiddler resigned the requests with a different certificate, the app terminates the connection believing that there is a man-in-the-middle attack (which is technically true).
In summary:
Hi im following all the above steps but still not able to get traffic from all apps. Im using Huawei Mediapad 7 Youth.
Below is the difference that i encountered while performing the steps.
The above screen shot “Name the Certificate” is displaying “The package contains: 2 CA certificates” but when i am trying i am getting a message “The package contains: one CA Certificates”.
Is this the reason some apps are not working.
I don’t think that it saying “The package contains: one CA Certificates” would be the reason for it not working. As long as you have the add-on installed for fiddler to create certificates for mobile devices then it should work. Telerik may have updated the add-on since I wrote this post, in which case, it could have just changed.
Definitely check that you installed the add-on. If that doesn’t work, I have noticed that certain Android manufacturers modify the Android os in a way that prevents any 3rd party CA Certificates to be installed without rooting the device.
The only Android manufacturer I’ve personally seen this in is Sony. But my exposure to Android brands is fairly limited.
Unfortunately, there’s a huge problem w/Fiddler certificate on Android. The system will display a warning that the network may be monitored, prompting the user to uninstall Fiddler certificate from the system. The only way to get rid of those warnings is to root the device and move the certificate from user to system folder.
I’m using Fiddler for surveillance purposes, so this problem is quite serious.
Hell,
I have problem with CertMaker.
It works great, but if I drop IOS program, then it not decrypts traffic and shows error in log:
!SecureClientPipeDirect failed: System.Security.Authentication.AuthenticationException A call to SSPI failed, see inner exception. < An unknown error occurred while processing.
Thank you in advance